
gmailc2: Unveiling the Powerhouse of C2 Servers Based on Google SMTP
Are you looking for a robust and undetectable C2 server? Look no further than gmailc2, a powerful tool that leverages the stability and widespread acceptance of Google SMTP to facilitate secure and untraceable communication. In this detailed guide, we will explore the ins and outs of gmailc2, its features, installation process, and best practices for using it effectively.
Understanding the Basics of gmailc2

gmailc2 is a C2 (Command and Control) server designed to enable secure and undetectable communication between a malicious actor and their compromised systems. By utilizing Google SMTP, it bypasses common network restrictions and antivirus detections, making it an ideal choice for those seeking a stealthy communication channel.
Here’s a quick overview of the key features of gmailc2:
| Feature | Description |
|---|---|
| Persistence | Ensures that the C2 server remains active on the compromised system, even after reboots or system updates. |
| Shell Access | Allows the attacker to execute commands on the compromised system, providing full control over the infected machine. |
| System Information | Collects and sends system information to the attacker, including hardware specifications, installed software, and network details. |
| Stealthy Communication | Utilizes Google SMTP to bypass network restrictions and antivirus detections, ensuring that communication remains undetectable. |
Setting Up Your gmailc2 Environment
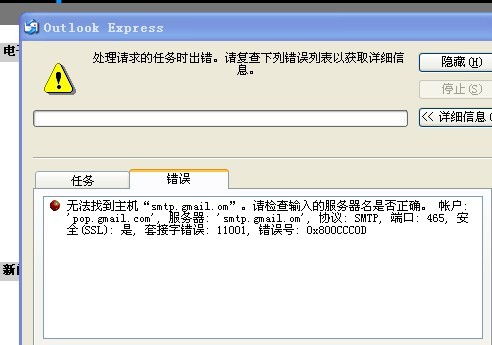
Before you can start using gmailc2, you’ll need to set up your environment. Here’s a step-by-step guide to help you get started:
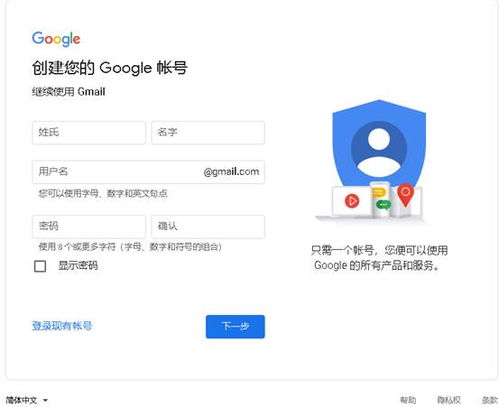
- Create two separate Gmail accounts. Let’s call them Account A ([email protected]) and Account B ([email protected]).
- Enable SMTP on both accounts. This can be done by logging into your Gmail account, navigating to the “See all settings” link, and then scrolling down to the “Accounts and Import” section. Click on “Add another email address you own” and follow the instructions to enable SMTP.
- Clone the gmailc2 repository from GitHub using the following command:
- git clone https://github.com/machine1337/gmailc2.git
- Install the required dependencies by running the following command:
- pip install -r requirements.txt
- Open the server.py file located in the gmailc2 directory and fill in the following information on line 67:
- smtpserver “smtp.gmail.com” (do not modify this line)
- smtpuser “[email protected]”
- smtppassword “YourPasswordForAccountA”
- smtpport 587
- serverip “YourPublicIP” (replace with your actual public IP address)
- serverport 8080
Using gmailc2 for Secure Communication
Once you have set up your gmailc2 environment, you can start using it for secure communication. Here are some tips to help you get the most out of the tool:
- Use strong, unique passwords for your Gmail accounts to prevent unauthorized access.
- Regularly update your system and software to ensure that you have the latest security patches.
- Be cautious when downloading and executing payloads on your compromised systems.
- Monitor your network traffic for any unusual activity that may indicate a compromise.
Conclusion
gmailc2 is a powerful and versatile C2 server that can be used for secure and undetectable communication. By leveraging the stability and widespread acceptance of Google SMTP, it provides a reliable and stealthy communication channel for malicious actors. However, it’s important to use the tool responsibly and ensure that you have the necessary permissions and knowledge before proceeding.



